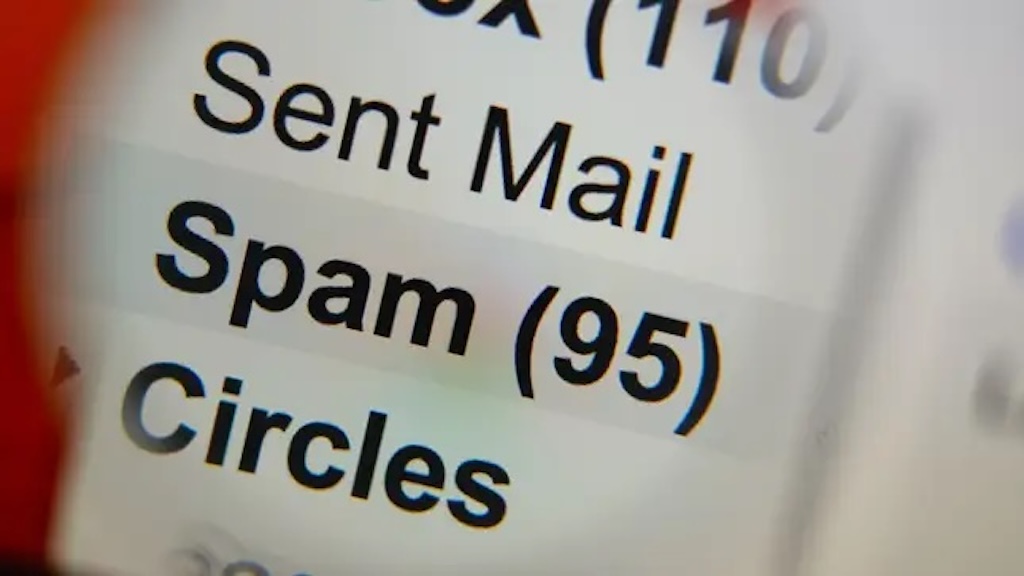
In August 2023 I posted on the junk mail (spam) I received over a one month period. During that period I was receiving between 15 and 30 junk/spam emails daily.
In early 2024 I received over 400 junk/spam emails in 10 weeks. So it looked like the effort I made in autumn 2023 to block as many as I could, was working.
Now in early 2025 I received a total of 438 junk/spam emails in 30 days. So a new surge in junk/spam emails!
Receiving junk/spam is a pain, but the real problem is phishing, a form of social engineering and scam where attackers deceive people into revealing sensitive information or installing malware such as ransomware. Phishing is now the most common type of computer crime.
Fortunately I don’t get any SMS or sales texts on my iPhones, so have avoided “smishing” scams so far (just one of many types of phone fraud). In any case I would always apply the ‘don’t text back’ rule. Never respond (or click on any links or call any phone numbers) in suspicious or unsolicited text messages. Immediately delete the message.
‘Never respond’ is also excellent advice for any type of unsolicited email, message, phone call, etc. And never, never click on links or open attachments from unknown sources.
Signs that something is wrong:-
- The message requests personal information, such as a credit card number or account password
- The message is unsolicited and contains links or an attachment
- If you’re prompted to download software
- The sender’s email address or phone number doesn’t match the name of the company it claims to be from
- A link in a message looks right, but the URL doesn’t match the company’s website
- The message looks significantly different from other messages you’ve received in the past (e.g. different presentation, email, contact phone number, spelling mistakes,…).
Remember scammers can use fake Caller ID info to spoof phone numbers, and often claim that there’s suspicious activity on your account or device to get your attention. What this means is that the callers appears to be a number you know, e.g. from your bank, etc., when in fact it’s a fake.
To focus the mind, let’s look at a simple example. You might receive an email from Apple Store or Amazon (as very credible examples) that inform/warns you that because you recently reset your password, before a new purchase can be made, you need to reverify the change. Or they say that the recipient’s ID/password was used to make a first purchase using a new device or a new password, etc. Scammers even offer to change the users’ password if they did not make the purchase. The webpage or website looks very credible, and they provide a link or a simple attachment where personal data (logins, passwords) will be ‘verified and confirmed’.
Another convincing scam mentions that they have detected unauthorised login attempts to your account. And there is still some information missing on your account settings. You should immediately correct and complete the information, and to make it easier and more secure “please click on the link to our special security webpage”. They might even threaten that they will be forced to disable your account if you don’t act quickly. Here is an extensive review called What is “Apple Email Virus”?, which describing typical attacks sent using fake Apple emails.
So never click through to new webpages or open attachments, even on emails that might look credible. Always be suspicious!
Different types of junk/spam/scam
Wikipedia defines junk mail as advertising material that lands in someone’s physical or digital in-box. The implication is that it comes from legitimate sources as direct marketing, often non-profits organisations and political campaigns are mentioned. Defining it as junk implies that the mail was unsolicited and is unwanted.
Another definition is that junk mail comes from opt-in services (e.g. business advertising), whilst spam refers to messages that the user did not opt to receive.
Wikipedia defines spam, as unsolicited messages sent in bulk by email (spamming). Some spam can be simple commercial advertising, or attempts to inform/convince about a political or religious problem or ideology (often now called attention theft). However, the real problem with spam is that it could be phishing, where attackers deceive people into revealing sensitive information or opening file attachments which install malware.
A scam just means some kind of fraudulent or deceptive action, but is usually seen as a dishonest or illegal plan or trick to ‘con’ or swindle people out of money. Some types of scams don’t directly involve money, but are designed to collect personal information that can be used in identity theft. This information includes a person’s name, date of birth, social security number, driver’s license number, bank account or credit card numbers, PINs, electronic signatures, fingerprints, passwords, or any other information that can be used to access directly or indirectly a person’s financial resources.
How to tell if it's a scam?
There are some very clear signs that it’s a scam.
Scammers PRETEND to be from an organization you know.
Scammers often pretend to be contacting you on behalf of the government (so-called imposter scams). They might also use a real name associated with your bank, tax authority, insurance company, etc., or make up a name that sounds official. Some pretend to be from a well known business such as a utility company, a tech company, or even a charity asking for donations.
They often will try to use a credible sounding email address, or use technology to change the phone number that appears on caller ID. So the names and numbers might not be real.
Some scammers try to exploit a common social-personal problem, e.g. unexpected bills, job loss, heath problems, poor credit rating, debt relief, car or house repairs, etc., and they often highjack logos, webpages, etc. of well known agencies or charities.
As an example I recently received a very convincing looking email about me not having paid a speeding fine. But a quick check of the sender email showed that it was clearly a scam email.
Don’t be fooled simply because the sum of money involved is small, e.g. a few 10s of €.
Scammers say there’s a PROBLEM or a PRIZE.
They might say you’re in trouble with the government. Or you owe money. Or someone in your family had an emergency. Or that there’s a virus on your computer.
Some scammers say there’s a problem with one of your accounts, and that they need you to urgently verify some information. They can mention any type of account that might hold bank and credit card information, e.g. Amazon, Apple (iCloud), Netflix, etc.
Others will lie and say you won money in a lottery or sweepstakes but have to pay a small administrative fee to receive the winning in your bank account.
As an example I received a very stupid looking email from @icloud with a email from a credible sounding travel magazine. But with a very poorly edited message highlighting 42 complaints about my email account, and the advice that I should ‘scan for viruses’. Be warned that many of these type of scam email are professional edited and can look very convincing. More or less at the same time I received an even more convincing message from Apple-iCloud-Team with an ‘membership’ email, about upgrading my ‘Apple Account Storage’, and offering to “Activate My Free Storage”. A better looking scam, but still a scam.
There was also a iCloud spam/scam from a totally stupid email address, who was also behind spam/scam emails for Google Notice and Netflix.ID. And another iCloud spam/scam also came from the nice sounding ‘woman…….’.
Scammers PRESSURE you to act immediately.
Scammers want you to act before you have time to think. If you’re on the phone, they might tell you not to hang up, so you can’t check out their story.
They might threaten to arrest you, sue you, take away your driver’s or business license, or deport you. They might say your computer is about to be corrupted.
Anything to underline “you must act NOW”.
Scammers tell you to PAY in a specific way.
They often insist that you can only pay by using cryptocurrency, wiring money through a company like Western Union, using a payment app, or putting money on a gift card and then giving them the numbers on the back of the card.
Some say they will send you a check (that will later turn out to be fake), then tell you to deposit it and send them money. But all you have to do is now pay to cover the ‘administrative costs’. If it sounds-too-good-to-be-true, it’s because it’s a con.
Remember scammers want someone to click through the email, and onto their website or into their application, which allows them to create a richer (read ‘more convincing’) customised experience (read ‘con’). And it’s in these websites and applications that scammers collect sensitive information and/or steal money.
The US Federal Trade Commission has excellent consumer advice on identity theft and online security.
Here is a good example for a ‘free quote’, with an email received from your name.
This is an example of email spoofing where scammers send emails that appear to come from your own email address or include your name in the sender field.
Email protocols (like SMTP) allow senders to specify almost any “From” address. Scammers can manipulate this field to make it look like the email is coming from you or someone you know. They can use compromised mail servers or their own servers to send these spoofed emails. In some cases the email address comes from a data breach or online directory, which scammers use to personalise phishing emails. Even if they can’t fully spoof your address, they may set the display name to your name while using a different (but similar) email.
If you own a domain you can enable SPF (Sender Policy Network), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting and Conformance). You can check who is the real sender in email header “return-path” and “received” fields.
Never reply to, or click on links, which have your name in them.
Fake unsubscribe links
One important point is to look for fake unsubscribe links. Service providers will often oblige marketers to include an easy to locate unsubscribe link in every message. Not adding these buttons can be a violation of the terms of service. These buttons are usually found at the bottom of a message. The problem is that some legitimate marketers either break this rule or make the link very difficult to find. Some just unsubscribe you from that campaign, and add you to all their other campaigns.
We must continue to stress that you should not reply to suspicious emails or click on links or open attachments in emails you are not absolutely sure about.
Also spam emails will almost always include very official looking unsubscribe links, that are fake. Replying or unsubscribing to junk/spam risks triggering more spam or even exposing you to scams or malware. Clicking on a fraudster’s unsubscribe will simply confirm your email address is valid and active, and will probably result in your email appearing in lists offered for sale. They think that if you are willing, and take the time, to click on an ‘unsubscribe’, you might be willing or stupid enough to click on their scam as well.
Some unsubscribe links want you to go and input the ID and password you used for that site. Never do this, it’s almost always a fake unsubscribe.
It is possible to look at the address embedded in the unsubscribe link without opening the link. Often the link address is incomprehensible or obviously unrelated to the supposed sender (of the junk/spam/scam). This is another warning sign that the email is suspicious or worse.
How To Avoid a Scam?
Block unwanted email addresses, calls and text messages. Block unwanted calls and filter unwanted text messages.
Never give personal or financial information in response to a request that you have not been able to verify. Honest organisations won’t call, email, or text to ask for your personal information, like your social security, bank account, or credit card numbers.
If you get an email or text message from a company you do business with and you think it’s real, it’s still best not to click on any links or open any attachments. Instead, contact them using a website you know is trustworthy. Or look up their phone number. Don’t call a number they gave you or the number from your caller ID.
Resist the pressure to act immediately. Honest businesses will give you time to make a decision. Anyone who pressures you to pay or give them your personal information is a scammer.
Scammers will tell you how to pay. Never pay someone who insists that you can only pay with cryptocurrency, a wire transfer service like Western Union, a payment app, or a gift card. And never deposit a check and send money back to someone.
Stop, do not reply, do not pay, and talk to someone you trust. Before you do anything else, tell someone, e.g. a friend, a family member, a neighbour,…, what’s happened. Talking about it could help you realise it’s a scam.
My experience so far...
Frankly, in my experience some opted-in info-ads can quickly become spam. What happens is that I try to unsubscribe (i.e. opt-out), but I then continue to receive junk which has now become spam.
Definitions can be a bit pointless, but for me junk is stuff I don’t want to received, but comes from a legitimate source. And spam is something that is not what it appears to be, and could even be malicious.
It’s easy enough to send an email to junk, and to ensure that any future emails from the same source go directly to junk. But the reality is that many spammers will circulate through hundreds or more different email addresses, and you will have to block each address.
The biggest problem for me is that my filter occasionally put valid emails in my junk folder (about 5-10 valid emails per month are directed to junk). So I need to scan through my junk before erasing it, which is a pain-in-the-neck.
Most of my junk are commercial ‘offerings’ in one form or another. Occasionally one may be perfectly valid, but they have not implemented the unsubscribe message from me. Some mail is unsolicited but may be valid, however I don’t want to send an unsubscribe message to them. Sending an unsubscribe can have the exact opposite effect, making me a target for even more unwanted emails (or worse).
Quite a lot of this ‘commercial’ rubbish comes from US-looking websites selling US-type material and services. One specific category is US politically oriented spam presented as informative, etc. Examples include environmental action, gun control (both more and less), dealing with tax problems and the IRS, debt relief, … I’m not a US citizen and have never lived in the US, so all this is totally unsolicited. I certainly don’t unsubscribe from something I never originally subscribed to, I prefer to just block the address.
Another major category is ‘commercial’ spam/scam created by some type of on-screen form creation software, that also maintains email lists, creates automatic mailings and tracks replies, etc. Typical examples in my in-tray are pest control, roofing, solar panels, home repairs, pesticides and weed killer, health supplements, etc., all appear to be created and hosted from the same source. There are a couple that actually use Elon Musk for energy-saving devices, but it could just as easily be a fake reference to Walmart. A few actually mention “incredible discoveries” for prostrate cancer, etc.
Then there is the ‘commercial’ scam that piggy-back’s on valid topics and highjacks logos, layout, etc., and even copies all the legal small print. These are clearly scams. Typical examples in my in-tray are car rental and “we buy any car”, changing electricity or gas providers, cheaper house insurance,…
The major difference is that if sensitive data is obviously going to be needed (e.g. changing a standing order), then it is certainly a scam, e.g. phishing attacks. Other types of scams include messages about “reaching your storage limit”, being “selected to receive a brand new ….”, “cash back reward cards”, “you can win $500”, “pay off credit card debt”, “all-inclusive health insurance”, “improving credit score”,…
Malicious malware has the same overall objective (steal sensitive personal data), but the route is usually through downloading and installing software or an app, that captures sensitive personal information on the fly. I haven’t actually seen any emails asking that I download software or open apps, all I see is junk/span/scam webpages with links.
Of course some junk/spam/scam emails just promote “golden opportunities” or “ultimate offers”, without bothering to ‘offer’ anything precise.
One relatively common sub-set of malicious emails is “your subscription has expired”.
One specific category of malicious attacks are fake emails from delivery companies type UPS (or misspelt as USPS).
Another type of malicious attack asks for a signature to confirm a loan request.
And yet another offers a payment for completing an online survey.
One very specific type of malicious attack offers a same day “Concealed Carry Certificate” for a gun.
What I know about Apple Mail
As far as I know Apple Mail is managed by the iCloud Mail server, which is manually set up through a iCloud Mail account and accessed using an email client app.
The email client is automatically configured through iCloud Preferences in OS X, or through iCloud settings for an iPhone, iPad to iPod using iOS 7 or later.
Depending on when an iCloud account was created, the iCloud email addresses and aliases may end with @icloud.com, @me.com, or @mac.com domains. @mac is the oldest, then came @me, and @iCloud was introduced in 2012. Apple notes that once a @me.com or @mac.com alias is deleted it cannot be added again to an iCloud account.
Apple claims that iCloud Mail uses trend analysis, dynamic lists, and other technology to automatically detect and block junk mail before it reaches my inbox. Apple looks at what they call ‘user engagement’, if someone received mail but never replies or sends emails to that address, Apple Mail will consider those incoming email as spam. I understand that also Mail is far less likely to mark email addresses that appear in my contact list as spam. I’ve read that Apple uses Proofpoint for its blacklisted IPs (not sure how recent this information was).
Because junk mail is blocked before it reaches the inbox, we don’t really know how much junk/spam/scam is actually directed at our in-boxes. Marking emails as junk helps the system block future unsolicited mail. Occasionally a legitimate email is sent to junk, but you can mark it as legitimate, and ensure that it does not happen again (remembering that usually Junk is automatically deleted after 1 month).
The advice from Apple is clear. Don’t open junk mail, just send it to junk, and then delete.
When you open an email that looks like junk mail, it can alert spammers that their message was received and opened from an active email account.
On an iPhone or iPad you can turn on Protect Mail Activity (Settings>Mail>Privacy Protection). In macOS under Mail>Settings>Privacy there is also Protect Mail Activity. And in iCloud>Mail>Settings it is also possible to set Protect Mail Activity (it’s worth noting that Junk mail settings are different from using rules to manage emails).
Protect Mail Activity tells us that emails can include remote content that allows the sender to learn information about you. When you open an email, information about your mail activity can be collected without you knowing it, and without you being able to control what information is shared. The sender of junk/spam/scam mail can learn when and how many times you opened their email, whether you forwarded the email, your Internet Protocol (IP) address, and other data that can be used to build a profile of your behaviour and learn your location.
Apple describes how Protect Mail Activity works. It prevents senders, including Apple, from learning information about your email activity. When you receive an email in the Mail app, rather than downloading remote content when you open an email, Protect Mail Activity downloads remote content in the background by default regardless of whether you engage with the email. Apple does not learn any information about the content.
In addition, Protect Mail Activity routes all remote content downloaded by Mail through two separate relays operated by different entities. The first knows your IP address, but not the remote Mail content you receive. The second knows the remote Mail content you receive, but not your IP address, instead providing a generalised identity to the destination. This way, no single entity has the information to identify both you and the remote Mail content you receive. Senders can’t use your IP address as a unique identifier to connect your activity across websites or apps to build a profile about you.
One very specific feature of Apple Mail is “Hide My Email“, which creates unique, random email addresses to use with apps, websites, etc., so personal emails stays private. This is particular useful when creating a new account with an app, or sending an email to someone you don’t know personally.
I am a fan of Apple’s Mail Privacy Protection, and the way it anonymises contact with new email messages. For example, email senders can install tracking pixels which fire when someone looks at an email and its contents. Fortunately Apple’s Mail app fetches the message and all the images, but not necessarily immediately, and whilst tracking pixels fire, it no longer means that someone has actually opened the message (it is still sitting in the inbox unread). This does not stop senders tracking clicks, but it allows the email recipient to decided to engage with the sender, or not.
As an interesting aside, open rates were often used as a key benchmark since it indicated how many people ‘viewed’ or ‘opened’ a commercial email. When Apple’s Mail Privacy Protection was introduced the global average open rate jumped from 19% in 2021 to 32% in 2022, but ‘opened’ no longer meant ‘viewed’ (the click through rate of 1.5% has stayed more or less stable and might be a more credible indicator now). Generally it looks as if the privacy policies in Europe (and elsewhere) have reduced the bounce rates in part because of double opt-ins and in part because mailing lists are being cleaned up and better targeted (to avoid potential fines or risky court cases).
What can I do (more) with Apple Mail?
I think it’s important for someone to take the time to read through the security and privacy options offered by their mail server. It’s too easy to just following a guide, but the key is to try to understand how the mailer server and app work, and to knowingly implement the options offered.
Below I’ve listed a few links to recent descriptions of how Apple Mail works.
Mail User Guide, with its Mail Support website, and What’s new in Mail on Mac?
Apple Mail Is Actually Useful Now
How to use Mail on your Mac | Apple Support (video)
What’s new in privacy (video)
I’ve been using ‘Move selected messages to Junk’, which moves the junk/spam email to Junk. I “Enable junk mail filtering” under Mail>Settings>Junk Mail>Junk Mail Behaviours, and I automatically move the offending item to Junk. There is an ‘advanced’ setting under Mail>Settings, which I haven’t used… yet.
It is possible to block a spam email address. Under Mail>Settings>Junk Mail>Blocked it is possible to either “Mark as blocked mail, but leave it in my inbox”, or “Move it to the Bin”. What I would really like is just a ‘disappear’.
I try to regularly check my privacy settings, but I haven’t (yet) adopted email aliases (e.g. ‘burner’ addresses), nor do I use a third-party email filter. I do have some secondary email addresses which I don’t use, but it’s interesting to see the occasional junk/spam email addressed to them. And it’s easy to block them.
Dark Web monitoring
The Dark Web is World Wide Web content that exists on darknets, overlay networks that use the Internet but require specific software, configurations, or authorisation to access. Through the dark web, private computer networks can communicate and conduct business anonymously without divulging identifying information, such as a user’s location. The dark web forms a small part of the deep web, the part of the web not indexed by web search engines, although sometimes the term deep web is mistakenly used to refer specifically to the dark web.
A lot of legitimate unstructured and unformatted content can be found on the deep web, but it is also home to black markets, botnet, and other fraud-related services. ‘Products’ found in the black markets include hackers selling their services, address lists for spam/scam mailings, leaked credit cards, tools such as trojan horses or backdoors, compromises passwords, etc. And to make it all the more interesting some of the services and products on offer are also scams themselves, i.e. designed to scam, scammers.
One approach is to use a dark web scanner or monitoring software. As far as I can see Apple does not offer these services, however there are a number of third-party providers in the App Store. These services generally offer to ‘scan and discover’ any passwords or personal information that have been leaked in a data breach. For example, one service provider offers a decent review in “A Guide to Finding Out If Your Information Is on the Dark Web“.
However, Apple does offer a password monitoring feature. In simple terms what this does is match passwords stored in the user’s Password AutoFill keychain against a continuously updated and curated list of passwords known to have been exposed in leaks from different online organisations. If the feature is turned on, the monitoring protocol continuously matches the user’s Password AutoFill keychain passwords against the curated list.
I also implement systematically Apple’s automatic strong passwords.
Apple also published “Apple Platform Security“, which provides details about how security technology and features are implemented.
Apple's 'click to unsubscribe' banner
Warning: Some emails will include at the top of their page what looks like the Apple Unsubscribe banner with “This message is from a mailing list”. It’s a fake, designed to get you to think your using the Apple Unsubscribe service. In this case don’t click on the Unsubscribe button. How to tell? The fake banner is part of the email message, and not part of the Apple email header. In the examples I’ve seen the “Reply-To” address does not relate/map to the send header.
You may have noted that on some emails, just below the header is an unsubscribe banner with the message “This message is from a mailing list.” This is different from any unsubscribe options in the actual message. In the very brief description from Apple it looks like it is directed at legitimate mail lists, and is just a way to easily unsubscribe from the list directly in Mail.
This feature can be seen in Mail on macOS, and in iOS the same feature sits above the email header. What Apple’s unsubscribe does is firstly look for a special ‘List-unsubscribe’ in the header, which can contain either a web address, an email address, or both. Apple Mail ignores web addresses but if it finds a properly formatted email address it will show a banner at the top that says “This message is from a mailing list” with a blue ‘Unsubscribe’ link. Clicking on this link generates an email message to the address that’s found in the ‘List-unsubscribe’ header, basically similar to how clicking on a ‘mailto:’ link works, except that in addition to filling in the subject and body specified in the link (if any), Mail also adds its own note at the end with the subject of the message that it was sent in response to, and sends the message out immediately in the background. With a legitimate mailer, your email will be automatically removed from the mailing list.
There is nothing magical about this feature. The unsubscribe banner only appears if a ‘List-unsubscribe’ header is found with a properly-formatted email address. As far as I understand things a lot of bulk email does not include a properly-formatted email address. Legitimate mailing lists are more likely to, and the Apple unsubscribe banner just makes it easier to unsubscribe (to something you originally opted into).
And I repeat, never click on an unsubscribe link in a spam message. You just tell the spammer that your email address is valid and actively used. And you will get even more spam, and worse.
Bad bots and robot.txt
I’m a user of WordPress, and whilst I don’t use (for the moment) the plugin “Blackhole for Bad Bots“, it nevertheless offers an insight into what is possible. Bad bots are software applications that run automated tasks with malicious intent, and this can range from stealing website content to account hacking. A simplest definition of a ‘bad bot’ is just a bot that hits a WordPress site, consumes server resources, but has no benefit to the site owner.
What this plugin does is hide a trigger link to the footer of pages, posts, etc. Then a line is added to the robots.txt file that forbids all bots from following the hidden link. Robots.txt is the filename used for implementing the Robots Exclusion Protocol, a standard used by websites to indicate to visiting web crawlers and other web robots which portions of the website they are allowed to visit. Bots that then ignore or disobey the robots rules will crawl the link and fall into the trap. Once trapped, bad bots are denied further access to that particular WordPress site.
We have to remember that perhaps more than half of all internet traffic isn’t human activity. it’s bots. The more common types of bots are web crawlers, search engine spiders, chatbots, knowbots, spambots, email-address harvesters, Facebook bots, Twitterbots, votebots, etc. Many are very useful, and some are ‘bad’. They can disrupt a website’s functionality, slow down workflow, drive away users or customers, and even block completely access to the site (botnets).
A further level of protection can be provided by a CAPTCHA which identifies legitimate visitors and allows them to log in, make purchases, view pages, or create accounts. All these CAPTCHA services use advanced risk analysis techniques to tell humans and bots apart, sometimes without even challenging humans to prove they’re not a bot.
Some examples of junk/spam/scam
Below I’ve tried to collect together a few examples of the type of junk/spam/scam email I received during January 2025.
You've been hacked
The occasional “You’ve been hacked” message, and they have ‘compromising videos’ of me/you, which they will delete for $2,000 in bit-coins.
Alternatives are linked to “attempted log in” to X, etc. and all you have to do is click through to change your password (they give you a single-use password). And some actually comes from X.com which is owned by Musk.
Trump-related or similar
Some emails will try to exploit a recent political, social, or newsworthy item. This can range from campaign funding for Trump, Nancy Pelosi “membership drive”, etc.
It’s calm now (2025), but before the elections there were hundreds of emails “begging” for money, support, etc.
Order confirmation or delivery
This is a spam/scam email purporting to come from an organisation such as Amazon. It mentions order confirmation, or delivery, but does not specify the content, so it piggybacks on purchase you might have made recently.
Sometime it includes some kind of gift or winning, e.g. “your recent order comes with a $500 gift card”, etc., and all you have to do is claim it.
These look more like punters looking for idiots, in that the scammer often makes little or no effort to create a credible looking email address. I guess that basic idea is that people order lots of stuff online, and are prepared for the occasional delivery query or problem. They click through on anything that involves tracking parcels, etc., and are prepared to provide sensitive information almost without thinking. The basic message can involve scheduling a delivery, …
The PayPal scam is similar, and involved a ‘debit’ for a purchase, eg. Apple Air-pods.
Debt relief
These fake official-looking ‘services’ offer to help with credit card debt.
Loan confirmation
This looks like an official ‘service message’ email from a vaguely credible ‘something-credit’, with the need for an e-signature to continue your loan request. It will usually have your email address embedded in it somewhere, and the language will be quite formal and official sounding.
Alternatives sell “Immediate Load Approvals”, “No Credit Check”, so you can “get on with your life”.
Health related
This can include:-
- Something to do with Medicare (sometimes with an ‘eligibility check’).
- Different types of medicinal cannabis, often offered alongside other off-the-shelf non-prescription medication.
- Strange email sender addresses which include videos on nerve damage, overworked liver, blood sugar, gut health, aging tips, knee support, weight control, mental performance, haemorrhoids, “salt water” trick of over-night melt fat, shrimp is bad for the heart message, … I haven’t views the videos, but I presume they promote some type of scam.
- Some convincing looking emails offer service such as eyesight correction operations, treating knee pain, hair loss, health screening, on-line therapy, … The interesting common feature is that they all are sent from the same email addresses.
- One related type of scam email appears to be requests for donations, e.g. for the American Heart Association but with a very dubious “Reply-To” address.
Credit card related
Here we have offers from unknown credit cards (which may mention also Mastercard, etc.). My impression is that they are designed for people who can’t normally get a credit card. And they even offer “Fraud Liability Protection”.
Surprise gifts
Everyone likes a surprise gift.
One example was a $300 ‘promo reward’ for telling them about “your e-commerce experience”. It even had a (fake) unsubscribe link. This came from a ‘pharmacy’ with a ‘.ru’ address. How stupid can you be?
Another is a “government message” that “Recent economic factors may have positively impacted your home equity. You may be eligible for new funding opportunities”. Naturally the email address is not in any way related to the government or the topic in question.
Home repair and/or maintenance
Everyone needs some help or advice about repairing something in the home. Or it could be about routine maintenance.
There will almost always be a special offer, e.g. ‘free window quotes’ with promised discounts or a “buy one, get one free”. Other examples include solar panels, metal roofs,…
Fibre and 5G phone offers from unknown services and strange email addresses.
There are also the usual ‘home warranty” scams, from stupid email addresses.
Offers for one-year free electricity if you change your supplier. Not a stupid email address, just an incomprehensible one and unrelated to the senders highjacked trademark, e.g. Repsol,…
For some reason, over the years spam (or worse) emails have consistently come from “ADT-Security” (recently on smart locks). Or it’s a free quote for “smart home security”. The email addresses are constantly rotated, so its difficult to block them all.
Car related
This can involve:-
- Vehicle protection after the warranty has expired (usually sent from a total unprofessional email address).
- Insurance against costly car repairs (often with a doubtful email address).
- Auto injury claims, from stupid email addresses.
There are legitimate car sales sites, but there are also fakes. The best way to immediately tell the difference is in the reply email address, which usually does not match the supposed company name mentioned in the unsolicited email, e.g. the email often references car manufacturer such as Dacia, Honda, …
Trending products, discounts, etc.
This could be just junk (unsolicited), or worse. The email address might appear credible, and they offer hot products, discounts, weekly trends, .. Buyer Beware.
Job offers/on-line education
These are unsolicited emails with “We came across your profile and think you could be an excellent fit for a role we’re looking to fill”. The jobs ‘on offer’ are usually well-paid options but requiring little specific skills, e.g. “administrative staff” jobs. The format is simple, functional, and the email address might even sound credible, from the “xxx Group” with an email from the xxx-group.com.
Naturally they have a ‘Unsubscribe’ for something you have never subscribed to.
Or how to apply for a “masters” 100% online from what looks to be, or could even be a recognised educational institution, but where the email address does not correspond.
When you think you have seen it all...
You haven’t.
Here are a few more legitimate names that are used by scammers, AT&T, Costco, Washington Post, Hyundai, FreePrints, T-Mobile, MasterCard, Capital One, …
A final word of warning
We don’t live in a private world. Today, much of our social, personal, academic and professional lives are tied to online platforms where we interact with others who share similar views, goals and outlooks. You may see the online world as a social space, a marketplace, or a career tool, but others see it as a space to highjack other people’s identity and steal money.
Everything someone posts, shares, comments on, or promotes online, will inevitably find its way into the public domain.
You may think you have ‘locked down’ your privacy settings. But it can never be foolproof. Online social media sites are constantly upgrading and updating their privacy settings, sometimes making it easier for your contacts or ‘friends of friends’ to access your information. Social media sites archive everything, and it’s all searchable. Something you wrote or posted years ago can re-surface if the topic ‘trends’. Recruiters, managers, clients, investors, competitors, vendors, etc. all search online before making key decisions. Reputations can easily be damaged online, and it is almost impossible to repair such damage.
No one is safe, today there are fake gaming websites for children, that promise free gaming and in-game currency in exchange for personal information. These are no different from the scam website pretending to be real government websites, and asking for a fee to process official documents like passports and visas.
Everyone is a target. If your not one now, you are next in line. Never share personal information, such as your name, address, or phone number, with people you don’t know or websites that you are not absolutely sure about. If something appears to be too good to be true, it usually is. Never click on links in emails or messages without first validating their origin. Be wary of unexpected messages from individuals you care about or know, fraudsters sometimes act as family members, friends, or officials in banks, etc. Use strong passwords and change them regularly. If someone is asking for money or personal information, be suspicious. It is better to be careful than to provide important information that might put more of your personal information in danger. Both real friends and legitimate officials will understand your hesitation and refusal to provide the requested information. If in doubt, call them using a phone number you know is valid.
PS Using 'rules' to filter email in Mail on iCloud.com
I remember using rules to set up a filter in Mail on iCloud, but it felt too complicated to use to filter our junk/spam/scam.
But then recently I came across this article about how the country-code top-level domain ‘.tk’ had become associated with spam. Tokelau has a population of about 1,500 people but has up to 25 million uses of its country-code. And it would appear that most of those users are sending out junk/spam/scam’s. The key was that it cost nothing to register a new .tk domain, so when one domain was blocked they just registered (free) another one.
A kind of sub-issue is the fact Google is now offering .zip (and .mov) as a TLD. This might be a perfect fit for organisations specialising in file sharing, storage, and downloads, but many .zip domains are being registered that resemble a wide variety of internal company filenames. An address such as ibm.com/somepath/somefile.zip might be seen as a zip file from ibm, but it can hide a malicious attack. Other .zip domains include corporatepackage.zip, google-analytics.zip, microsoft-update.zip, microsoftupdates.zip, googledrivebackup.zip,.. When an address like ibm.com/somepath/somefile.zip is sent to someone, email and internet browsers, etc. could read the string ending in .zip as a URL, and automatically hyperlink it. The issues is even more complex, in that a perfectly legitimate .zip file can be sent by a legitimate user, and the file name can be resolved incorrectly and pass through the .zip domain owner. They can collect internal filenames containing project names, personal identifiable information (PII), geography and order or contact names and numbers, etc., all useful for a future attack.
So the question is can I set a rule to block all mail from a TLD such as ‘.tk’ or ‘zip’?
It is certainly possible to do this with the firewall on a corporate server, and some Internet gateways also block connections to malicious domains, IPs and URLs.
The problem is that Apple Mail does not allow “wild cards” for pattern matching.
What you can do is determine the sender’s Return-Path header field, as this is the mail server that they use to get the junk to you. I have found in practice that concentrating on a Return-Path pattern allows me to control dozens of emails from the same organization using different sender credentials and names.
It is just a case of looking for patterns in Return-Path server strings.
The Return-Path headers string is not configured by default in Apple Mail, and you must add it as a custom header at the bottom of the menu when you click the default From header selector. Check out Wild card in apple email rules.